Project Description
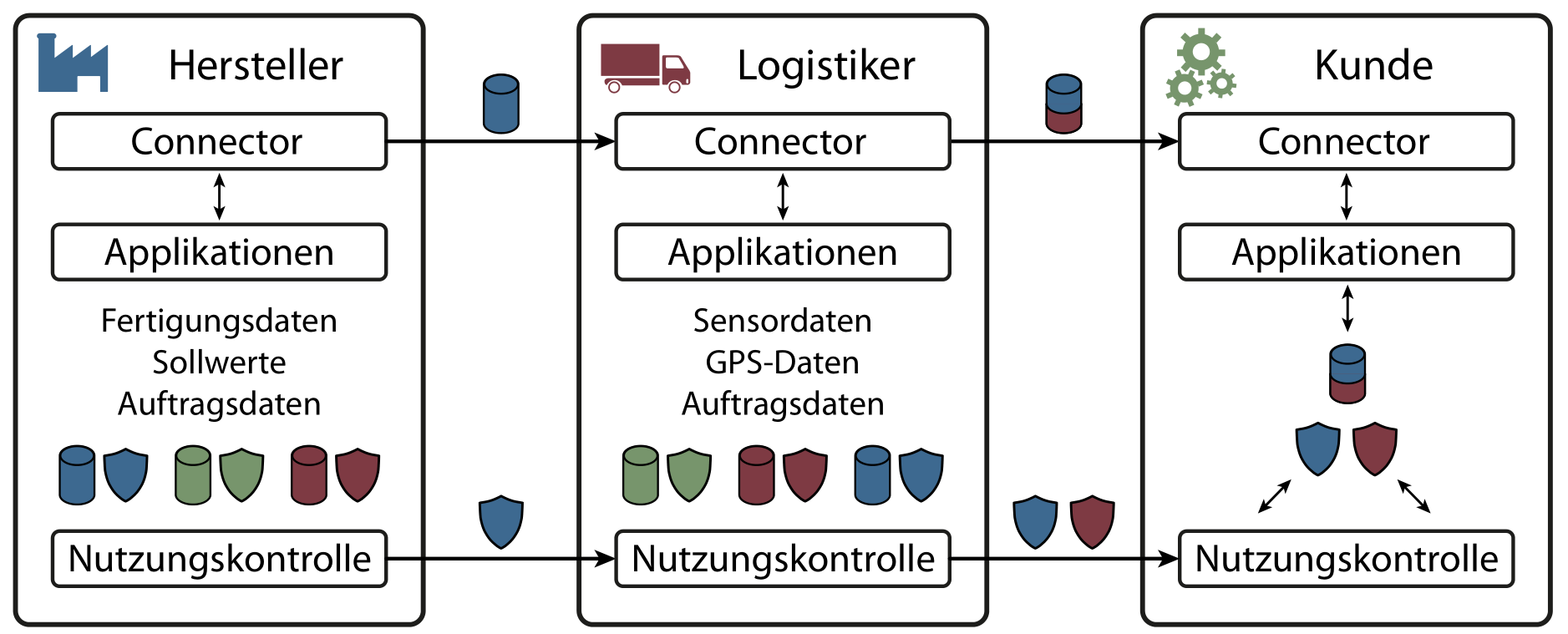
For many years digital innovation has been the main impetus for countless technological and economic developments. As a result of this development, data collection and sharing is now a foundation of many innovative and successful business models. However, since data have become invaluable assets in many use cases, large-scale sharing of information across corporate boundaries entails many new security challenges. In the past, data protection efforts mostly consisted of securing internal information processing infrastructure, like corporate computer systems and databases. Today, with complex data processing chains spanning over many collaborating corporations and across different countries, this isolated view on data security is not sufficient anymore.
In order to secure distributed data processing chains and enforce data sovereignty on a technical level, the application of usage control concepts became increasingly prominent. Usage control technology aims to restrict processing and distribution of sensitive data even after the data has been disclosed. This allows data providers to specify complex usage control policies and thereby restrain the future usage of their data. A secure implementation of distributed usage control systems requires establishing trust in remote protection components and preventing them from being maliciously manipulated. In most cases trusted computing mechanisms like trusted platform modules (TPMs) are used to achieve this. However, in distributed systems attackers often have quite comprehensive control over the technical systems, which complicates the proper verification of remote usage control infrastructures.
The goal of this project is to establish trust in distributed usage control systems purely by technical measures. In order to do so, new concepts and technologies have to be developed in the realm of trusted computing. Especially the ability of remote attestation protocols to preserve data sovereignty is one of our research focuses. Remote attestation protocols can be used to verify the integrity of protection components before disclosing sensitive information. The resulting trusted usage control systems act as building blocks for any data processing application that aims to guarantee confidentiality and data sovereignty on a technical level.